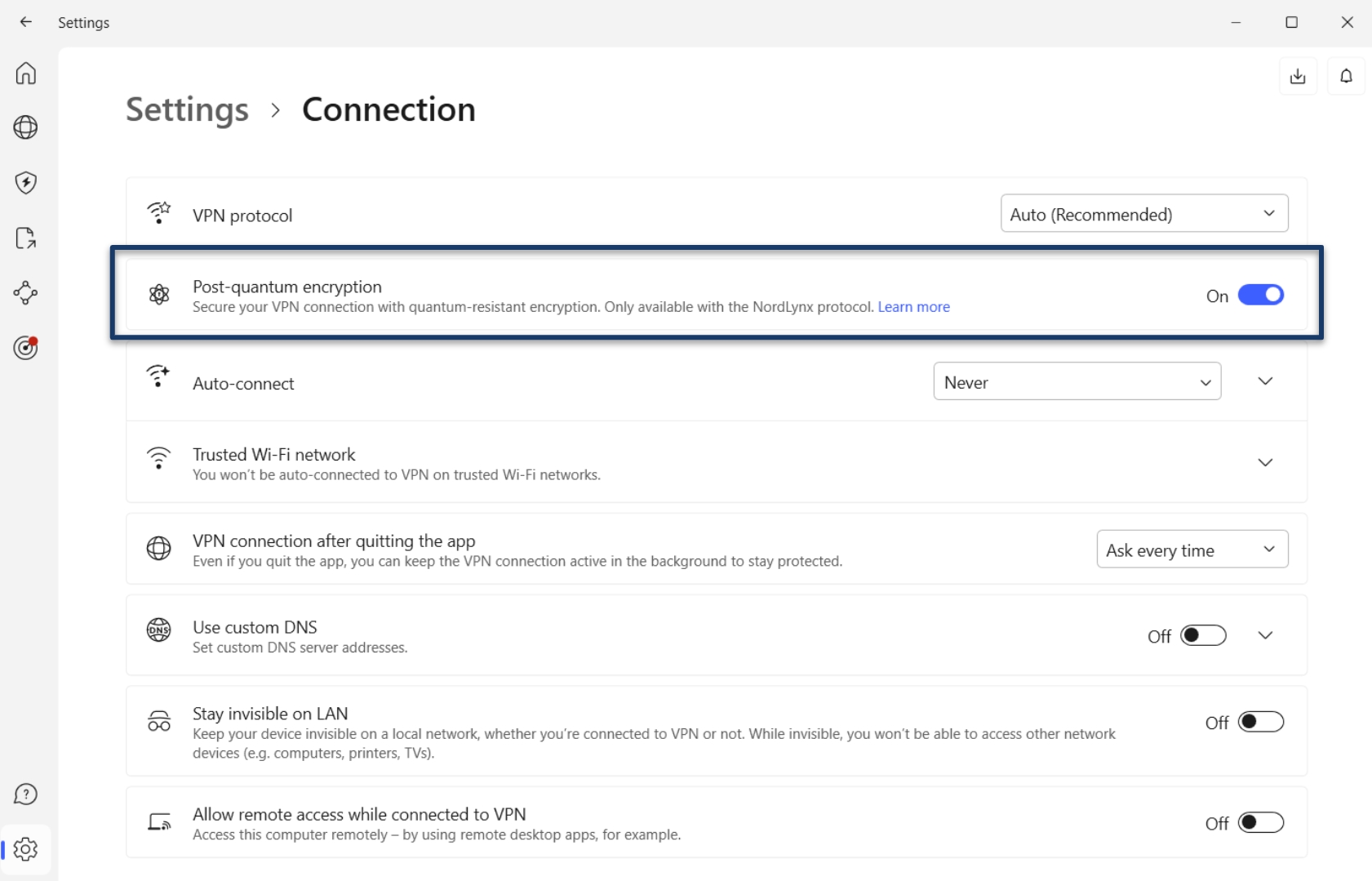
Leading VPN provider NordVPN has announced that it will roll out post-quantum encryption on all its major app-supported platforms. In NordVPN’s implementation, post-quantum encryption is integrated with its proprietary NordLynx protocol. Based on WireGuard, NordLynx is available on all of its
Latest News
Cybersecurity researcher Jeremiah Fowler discovered an unprotected cloud system exposing 184 million credentials. The collection, containing around 47.42 gigabytes of data, included sensitive information from popular platforms such as Instagram, Facebook, and Snapchat, as well as government
Crypto exchange giant Coinbase is reeling from a cyberattack that exposed sensitive customer data, prompted a $20 million extortion attempt, and could cost the company up to $400 million in remediation. The breach, disclosed this week via Coinbase’s official blog and a filing with U.S. regulators,
The White House has officially withdrawn a major data privacy proposal that would have made it harder for data brokers to sell Americans’ personal and financial information. The move reverses a key effort launched in late 2024 by the Consumer Financial Protection Bureau (CFPB) to crack down on the
Marks & Spencer has confirmed that personal customer data was stolen in the recent cyberattack that disrupted its services for weeks. The breach exposed names, addresses, phone numbers, and order histories. While account passwords and full card details were not compromised, the retailer urged
Google has agreed to pay a record $1.375 billion to the state of Texas to resolve lawsuits accusing the tech giant of unauthorized data tracking and biometric data collection. It marks the largest privacy settlement ever obtained by a US state. Texas’s payout surpasses all previous state-level
Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to vpnMentor about an unencrypted and non-password-protected database that contained 3,154,239 records presumably belonging to a platform designed to assist high school athletes in securing college sports scholarships. The
The cybergang behind a massive PowerSchool data breach is now attempting to directly extort schools and districts across the US and Canada — despite PowerSchool reportedly paying an undisclosed ransom for the deletion of the stolen data. According to BleepingComputer, PowerSchool was given
A federal jury has ordered NSO Group, the Israeli spyware firm behind Pegasus, to pay over $167 million in damages to WhatsApp for illegally hacking more than 1,400 users. The decision caps a six-year legal battle and marks the largest penalty ever levied against a spyware company. First
Cybercriminals behind StealC, a popular information-stealing malware, released a major update in March 2025, introducing new stealth capabilities and data theft tools. The update, detailed in a new report by Zscaler researchers, enhances the malware’s ability to avoid detection and steal sensitive